For several months this year, the world of finance, as well as the world of information technology, have been buzzing about a cyber security controversy. A major credit reporting agency was recently under a cyber attack that resulted in one of the worst leaks of personal information in history. Birth dates, social security numbers, addresses and driver license numbers of 143 million Americans were stolen. This event has shed some new light on cyber security issues, since it was later revealed that this breach was due to a software problem that could have been prevented had experts at the major credit reporting agency reacted in time.
To prevent breaches in cyber security at your business, you need to know how to monitor it.
How to monitor cyber security
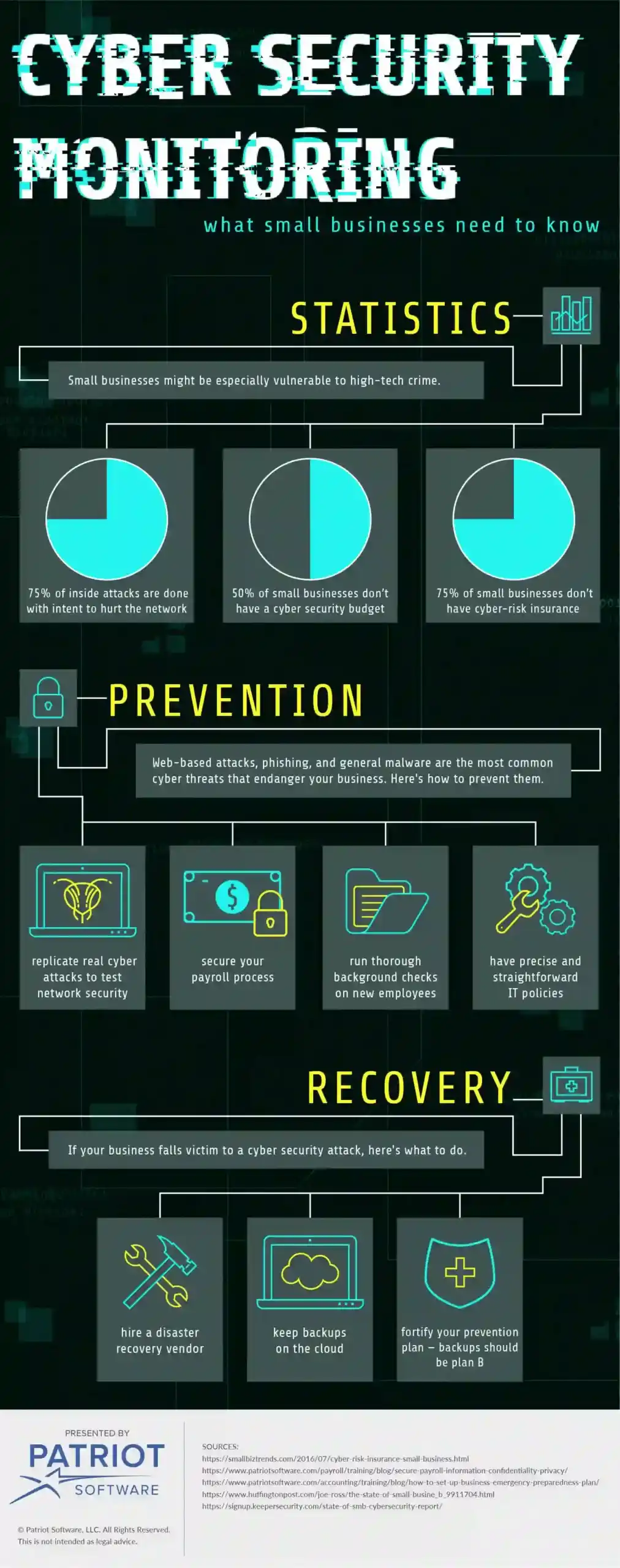
High-tech crime and data protection are huge issues for all businesses, both small and big. As a matter of fact, small businesses normally use more primitive protection systems and are thus more vulnerable.
Two facts from around the globe are especially worrying – in the UK, 74% of small organizations have experienced some kind of security breach, while in the US, 75% of small businesses don’t have any kind of cyber-risk insurance. This should be alarming if you run a small business yourself, and if that’s the case, here are a few things you should know.
Business continuity
Your most important objective is to ensure business continuity – that is, to make sure that your organization continues to operate as soon and as smoothly as possible after the attack. If you don’t want your business to start losing money, you’ll have to get it up and running in no time.
An average loss following some type of network downtime is startling – around $5,600 per minute. In order to prevent this, you need a good cybersecurity strategy that can basically be divided into two parts – prevention and recovery. First, let’s take a look at what you can do to prevent unwanted occurrences in your network.
Penetration testing
A good way to detect possible issues and dangers in your network is penetration testing, and these tests should be run on a regular basis. The test involves replicating real cyber attacks to see how secure your network is and how it reacts when put under actual threat. Look at it as a kind of military exercise – you want to test your system’s abilities and endurance without engaging in actual combat, or in this case, without putting the network in actual danger.
Most common threats
There are all sorts of cyber threats that can endanger your business, with web-based attacks, phishing, and general malware being the most common ones. But, in order to learn how to prevent and solve all these problems, it’s important to look at their most common causes.
Inside dangers
Sixty percent of all cyber attacks come from inside your company, whether they are intentional or accidental. This basically means that your employees pose one of the biggest cyber security threats for your business. What can you do about this?
It’s important to know that 75% of these inside attacks were done with an actual intent to hurt your network. So, to prevent these incidents from happening, securing your payroll process and running thorough background checks on new employees is a must. As for the others who simply made accidental mistakes, a good way to prevent these mistakes from happening again is having precise and straightforward IT policies and procedures that all employees have to follow. You also need to carry these policies and procedures out properly.
BYOD risks
BYOD (bring your own device) policy looks like a reasonable choice at first glance – if employees work on their own devices it not only cuts your costs, but it might also be more convenient for your employees to use the same computer they use at home. However, when you integrate all these devices into one system it becomes very vulnerable since hackers normally target users, not servers. Therefore, if any of your employees downloads malicious software, loses a phone, or has device that is easy to attack, your network and business are in danger. It’s very important to acknowledge this and make additional security efforts to stop this from hurting your network.
Recovery
If your security strategy failed after all and you didn’t manage to prevent a serious attack, then it is inevitable to employ the second step – recovery. Of course, having a backup is essential, and it is becoming simpler to keep backups as cloud computing is more advanced and cheaper.
When it comes to the process of restoration, you should be concerned about where and how you store your data and business emergency preparedness strategy. It’s thus advisable that you have a disaster recovery vendor and put the whole process of information storage, duplication, and recovery into the reliable hands of experts in the field.
However, a backup is just what it is – a backup. It shouldn’t be your Plan A. You should always have a sound plan on how to prevent attacks. Reaching for backup should be done only if everything else fails. Almost 60% of small businesses are concerned about the security of their network, but at the same time, around 50% of them don’t have a cyber security budget at all. It’s crucial to recognize that the key to successful monitoring and protection of your network is to take constant care and be alert at all times. This is only possible if you adopt the right, custom-made security strategy and implement it properly.
These views are made solely by the author.



