Well, it’s official. Phishing attacks are on the rise. In 2021, 83% of organizations faced a successful email phishing attack. And here’s the other side of the coin: phishing is expensive. These attacks cost large organizations nearly $15 million annually. And because small businesses are three times more likely to be targeted by cybercriminals than larger companies, it’s time to protect your organization.
So what is phishing, exactly? How does it work? And, how can you protect your small business from phishing attacks?
What is phishing?
Have you ever opened an email urging you to take action, like clicking a link to log into your bank account or providing personal information? If so, you’ve seen phishing attacks in action.
Phishing is a type of social engineering attack where the sole purpose is to gather as much sensitive information as possible using email. The emails are fraudulent but appear to be from a reputable source. The goal is to dupe the person into believing that the email is legitimate so that the bad actors can get hold of or divulge the person into providing sensitive information.
You may also see phishing attacks carried out over text messages, a phenomenon known as smishing that’s becoming more common.
Keep in mind that phishing isn’t the only type of cyberattack you could see at your business. Other common types of cyberattacks include:
- Denial of service (DoS) or distributed denial of service (DDoS) attack
- Man in the middle attack (MitM)
- Malware attack
How does phishing work?
The goal of a phishing attack for the cybercriminal is to gain access to important accounts (e.g., bank accounts) or gain enough of your personally identifiable information (PII) to sell to scammers. To accomplish this goal, they need your information. And in business, no owner wants a PII breach.
Phishing attacks attempt to steal information such as your:
- Passwords
- Account numbers
- Social Security numbers
So, how exactly does a phishing attack work to get this information? Take a look at the basic phishing attack process:
- First, the cybercriminals identify their target(s), usually through available sources on the internet (e.g., LinkedIn and sometimes using open-source intelligence tools)
- The cyberattacker then creates an email that appears to be from a legitimate source
- These emails contain either a dangerous URL which, upon clicking, takes the user to a scam website or an attachment that may download malware onto the user’s system
Example
Let’s say you receive an email from someone claiming to be your bank that looks something like this:
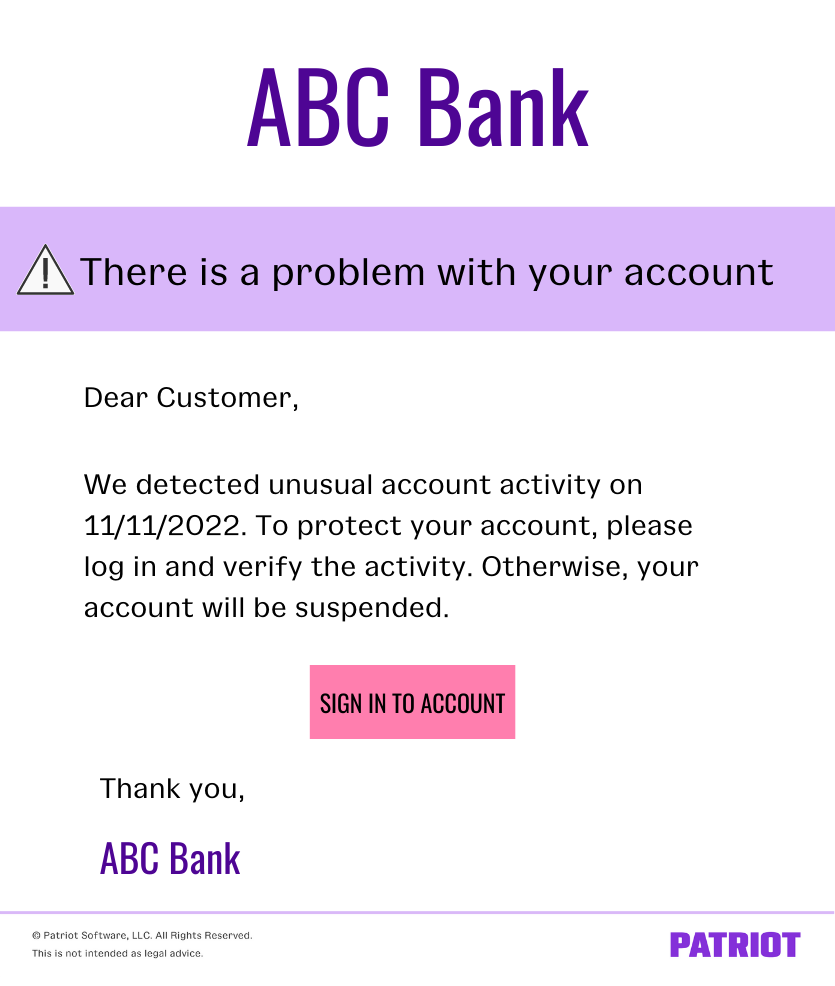
You click the button to log in and go to a website resembling your bank’s login page. You enter your bank username and password. No worries, right?
Wrong.
Here’s the truth: It was a phishing attack, and the website is fake. And now, the sender has your bank account username and password.
How can you protect your business from phishing?
No business owner wants to worry about phishing attacks. But, they happen. Understand how to safeguard your business from tax scams and other phishing attacks.
More and more companies have shifted online, thus putting them at risk of a cyberattack. IT security (a term that is used to describe controls that are put in place to protect IT systems, data, data processing, and storage from unauthorized access) controls are put in place to ensure the confidentiality, integrity, and availability of data and information.
There are a few ways to prevent phishing:
- Don’t click on any link received from an unknown source
- Don’t follow any instructions that encourage you to urgently visit a website
- Never provide your personal information, such as username, password, etc.
- Finally, trust your instincts, if something feels wrong it likely is
REMEMBER: Think before you click.
Check out the Federal Trade Commission website for more information on recognizing and avoiding phishing scams.
This is not intended as legal advice; for more information, please click here.
